The weak link
Ever since I had my Twitter handle changed to @0x back in January of 2010, I have been no stranger to attempts at stealing the account off me. First, it was seemingly lame password reset attempts - I got the emails, and simply ignored them, and then it escalated to straight up demands to surrender the address via subtle threats in my DMs.
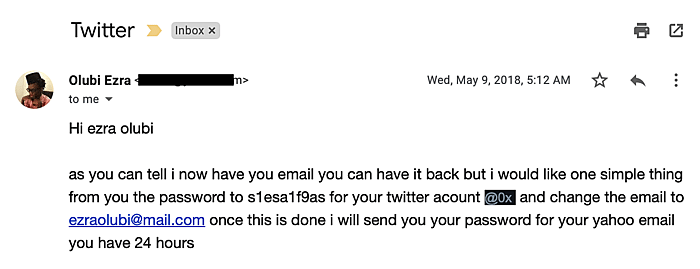
Sometime in 2018, someone succeeded in breaching my old and abandoned yahoo email account and then emailed me from the address, asking me to change my Twitter password to a specific text, along with what to set the new email address on the account to. I didn’t respond - he later reached out via DM threatening to leak compromising pictures he had in his possession from the breach.
I didn’t think I had anything to be worried about. My security sense is definitely not fort knox level but at least, I had all the bases covered - I use a password manager, and I have 2FA setup everywhere that mattered - or so I thought. I woke up on the morning of the 25th of May 2019, realizing how monumentally wrong I was.
About two months prior, I flirted with the idea of migrating my phone number from T-Mobile to Google Fi. I didn’t - choosing to leave it till later. At the time, I saw it as a vanity act I could get to at a later date. I got to it eventually - but not before my line got SIM-jacked and paved way for a complete theft of my online identity.
How it unfolded #
The domain name I use with my personal email address was bought on GoDaddy back in 2007 and has been on that account ever since. I manage the DNS using Cloudflare and as such, only login to my GoDaddy account about once in two years to renew the name alongside other domain names I have bought over the years.
Sometime in the third week of May 2019, my T-Mobile line lost cell service. I am not sure of the exact date as I used the line early in the week to make some calls but ignored it afterwards. I was in Nigeria at the time and wasn’t making regular use of the line.
My attacker (let’s call him Jeff) proceeded to reset my GoDaddy password by convincing the support personnel that he had lost access to the email address but could have his identity verified using my phone number. I didn’t have 2FA setup on my GoDaddy account so this was relatively frictionless. Jeff eventually got into my account around 11:34PM WAT on the May 24.
Now in control of my GoDaddy account, Jeff proceeded to change the email address on the account to [email protected] and setup 2FA. He then modified the nameservers for the domain name from Cloudflare’s to GoDaddy’s after which he bought an Office365 addon (using my saved credit card details no less) with the intention of setting up a mail service he could use to impersonate me. Seeing as he was now in control of my DNS records, he was able to setup new MX records and just like that, all mails intended for me ended up in his new inbox, completely bypassing my G Suite account.
Now in possession of my phone line and my email address, he proceeded to reset everything he could lay his hands on. Well, as much as he could before I woke up.
On the morning of the 25th, I launched my Twitter app around 10AM only to be told I had to login. I wasn’t sure what was wrong at the time but after looking up my account in incognito and saw that it was locked, I promptly checked my mailbox and saw a password reset attempt on my Instagram account around 11:58PM WAT the previous day (the new MX records probably hadn’t been fetched by Facebook at the time) and absolutely no new emails from about two hours later. Quickly, I typed my domain name into a browser and was greeted by a default GoDaddy “success” page. That was when I realized what was going on.
Fuck.
I couldn’t login to my GoDaddy account. I discovered that my T-Mobile line was essentially a dud. My work email was still working and nothing work related appeared to be compromised yet. I quickly went to the account settings of my work email and removed all ties to my personal email address, starting with recovery options. I called Loknan, our Infrastructure and Security Lead and told him I had been compromised, directing him to immediately revoke all my access to company resources. A member of his team, Eyitemi was briefed and everyone was on high alert. Eyitemi handled communication to the company to let everyone know to ignore any form of communication from me until further notice.
I created a ProtonMail account and began resetting my identity on important services such as my password manager, financial apps, my bank accounts, etc. My Amazon account, Facebook/Instagram accounts, were already in Jeff’s hands at this point. All of these, including my Twitter account had (authenticator-based where possible) 2FA setup but that was not enough since they all also had my now compromised phone number.
Some services such as Coinbase insisted on sending a mail to the current email address before allowing an email change. Sounds good on paper, but in the face of what I was up against, it wouldn’t work. I will succeed in alerting Jeff to the account and then he’ll just compromise it anyway. Oh wait, some of the services whose email addresses I changed sent Jeff one final email confirming the address change so he had already been alerted anyway. He attempted a few password resets, including incessantly trying to get into my Coinbase account. Thankfully, it was my Nigerian phone number on that one so I kept getting text messages. For the rest of the day, with change to spare for the next day. No kidding.
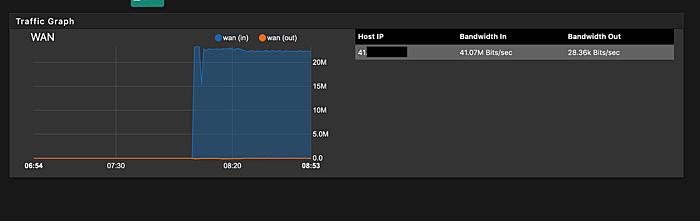
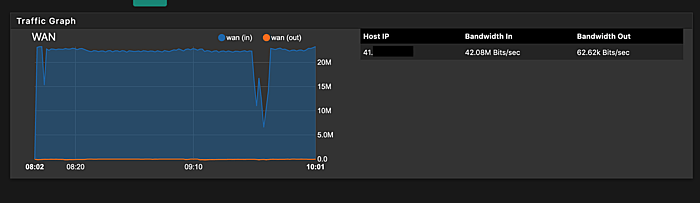
Just when I thought it couldn’t get worse, my internet connectivity slowed to a crawl in the evening and when I looked up traffic data on my router, this was what I saw.
I was being DDoS’d. It was surreal. I tightened my firewall rules and disabled port forwarding to services I hosted within my home network.
The timing couldn’t be more inconvenient. Monday the 27th of May was Memorial Day in the US and as such, most people had gone to see their family for the long weekend. Attempting to recover my GoDaddy account wasn’t going to be a straightforward process given my situation. Eyitemi managed to reach the VP of Engineering at GoDaddy who was helpful with escalating internally. I spent that night and the next day going through a fairly rigorous vetting process to establish my legitimacy. By noon on the 27th, I regained control of my GoDaddy account and in turn, my domain name.
In parallel, I had reached out to Twitter with regards to the locked account which it said was closed due to suspicious activity. I was asked to submit an ID to prove that I was 18 when I opened the account. To my surprise, they happily released the account afterwards. To Jeff.
I wasn’t so unfortunate with the other compromised services though. By Tuesday evening, I had regained control of them all. Of interest was my Amazon account which even though the rep that helped me tried to purge it of activities performed on it by Jeff, a few breadcrumbs were left. These helped me establish the fact that he had claimed a gift card worth $528.94 on my account and used it to make a bunch of purchases - to an Amazon Locker. I imagine Amazon’s process of validating CVV when you’re placing an order to a new shipping address made it impossible to use any of my cards on file. Thanks Amazon.
My Twitter account #
I was worried that my account’s DMs were now in the hands of a hostile party at this point. He was posting weird stuff on the account, presumably to prove to his Discord friends that he was indeed in control of the account.
I opened a new support request, explaining my predicament to what seemed like a robot run operation. On the off chance that a request seemed like it was reaching a resolution, my email address got added to the account at which point I was able to reset the password to the account. However, upon logging in, I had to go through an extra confirmation step to have my email address supplant Jeff’s. Unfortunately, I never received these emails. Eventually, Jeff would realize I had changed the password to the account and will just change it back, locking me out and leaving me to start all over again.
By mid June, he had reached out to the people behind the cryptocurrency, 0x (@0xProject) with the intention of selling the account. Thankfully, a member of the 0x team reached out using my work email address to inform me of this and to “make sure it wasn’t stolen from” me. I thanked them for reaching out and explained that I was indeed compromised and they should not humor the seller as I had every intention of getting my account back. For context, someone from the team had reached out earlier to me expressing their interest in the account. I had politely declined. I’m guessing that was when they had established who I was and knew to reach out to me when it seemed the circumstances had changed.
I grew more and more bored of creating new support tickets over time as the play was always the same. It didn’t help that on occasion, the rep just assumes I am the one trying to steal the account and closes the ticket.
I eventually gave it a try again two weeks ago with the help of my cofounder and a couple of people from our network and here we are today. I was connected to an insider within Twitter who helped with the process, including not just adding my email address back to the account, but also deleting Jeff’s. I also got around the problem I had with not receiving confirmation emails by deleting my email address and adding it back to the account.
I now have the last piece of the puzzle in place. 1 year later.
Lessons learned #
SMS-based 2FA is a joke. No, seriously. Use an authenticator app wherever possible.
Your security is only as strong as your weakest link. Mine happened to be the lack of 2FA on my GoDaddy account.
Thanks to Loknan Nanyak, Cynthia Ndeche, and Oiza Jagun for reading drafts of this.